What makes Gurucul stand out among the many security analytics vendors? Well, for starters, Gurucul’s behavior-based predictive security analytics takes security beyond SIEM. Read on to learn how Gurucul is leading an evolution from black box analytics to machine learning and risk scores.
Back in the SIEM Age
Coined by Gartner in 2005, the term SIEM was used to describe Security Information and Event Management software, which provides a real-time analysis of security alerts. However, that was 15 years ago, and a lot has happened within that time.
Traditional SIEMs import data, normalize that data and provide minimal enrichment (details). Correlation rules specify a sequence of events that indicates an anomaly, or potential security threat. The reason why Gurucul believes this technique is outdated is because it generates significant amounts of false positives. Also, it is incapable of detecting new, and especially, unexpected threats. What if you had the technology to predict a breach before it happens?
Normalization was necessary in the early days of SIEM, when storage and compute power were expensive commodities. Back then, SIEM platforms were using relational database management systems for back-end data management.
Our competitors tout themselves as “Next-Gen” SIEMs because they offer analytics and not just logging. And while they might add a little more functionality to the mix, they are proprietary. They only see what they put in and it’s up to the vendor to choose what to enrich. Analytics may add value but the output from the models are black box analytics. Results are taken on faith, because no one knows how the answers are obtained, or if they are even valid.
Think Outside the Black Box with Gurucul Behavior Analytics
Taking security beyond SIEM capabilities requires thinking outside of the (black) box. Gurucul uses behavior-based security analytics powered by machine learning to detect risky behavior, whereas SIEMs follow rules and correlations. For example, Fred Jones might be on his way out of your organization and planning on taking some confidential information with him. With a SIEM, you might not pick up on the fact Fred Jones is sending internal documents to his personal e-mail or visiting job sites. But with Gurucul, our behavior analytics capabilities will detect the strange behavior and pick up on his anomalous activity that goes outside of the norm.
There is a lack of transparency surrounding black box analytics. Black box based analytics products generate alerts and risk scores, but there is no way of knowing what data goes into generating those risk scores. How do you know if these alerts are true positives? The false positives and the tedious work that comes with having to write rules sabotages productivity for the security operations team. That’s why Gurucul Behavior Based Predictive Security Analytics uses machine learning over writing rules and queries.
Gurucul offers open enrichment and open analytics. Unlike SIEMs, we show you exactly how our machine learning models work. Customers can customize our models or create their own. We give you full transparency into how we calculate risk scores and prioritize alerts. The days of black box analytics and crossing fingers are over!
How Does Gurucul Behavior Analytics Generate a Risk Score?
SIEMs generate alerts depending on correlation rules and queries. But Gurucul Behavior Based Security Analytics looks at behavior. As described above, in the Fred Jones example, behavior profiling is based on activity and access. The program is always taking in data and looking for a change in behavior patterns. The risk score reflects the result. The risk score isn’t just humans in your organization, it’s for entities and devices too. So, from the company computer you’re typing on to your company cell phone – they all have risk scores.
When it comes to SIEMs, correlation rules can only detect known patterns. So, the unknowns go completely undetected. In today’s digital age, as cyber hackers and criminals become more advanced, any time that passes between a breach and an alert is money. Gurucul’s machine learning algorithms learn as more data gets ingested – that is how we detect the unknowns.
Security Analytics Continues to Evolve from Correlation Rules on Relational Databases to Machine Learning and Behavior Analytics on Open Choice Big Data
So, here’s the current situation: your security applications and IAM systems are firing off alerts. But which alert is most critical? How can you tell?
Let’s say you’re using a Next-Gen SIEM, a PAM, an IGA solution or the like that offers analytics. The issue here is that the analytics are siloed, meaning that they are only being performed on data from that one application – on SIEM, PAM, or IGA data only. What are you going to do with all those alerts with zero context? It’s too noisy and there’s not context.
So, What’s the Situation with Gurucul?
We take unlimited data feeds from structured and unstructured security sources – SIEMs, firewalls, identity and access management systems, netflow and more. We can also gather context from your business applications – like SAP, EPIC, Salesforce or even your own proprietary applications on virtually any platform. All we need are transaction logs. It really is that simple.
We aggregate, link and analyze that data using our enterprise risk engine, providing a 360-degree view of users and entities. Gurucul tells you what they’re doing, where, when and with what entitlements.
Then, we generate a single unified risk score for every user and entity in your organization using behavior analytics. This is important because it enables you to focus on the highest risk areas in your organization. This makes it possible for you to automatically orchestrate downstream actions and apply automated risk-based controls.
There are many use cases for Predictive Security Analytics, which you can find in our UEBA use cases whitepaper. There you will get real-world examples of the benefits, such as:
- Predict and detect unknown threats
- Act on risk prioritized contextual alerts
- Automate responses with model driven security
- Reduce false positives significantly
- Diminish false negatives
- Radically reduce accounts and entitlements
- Provide cyber context and intelligence to eliminate cyber fraud
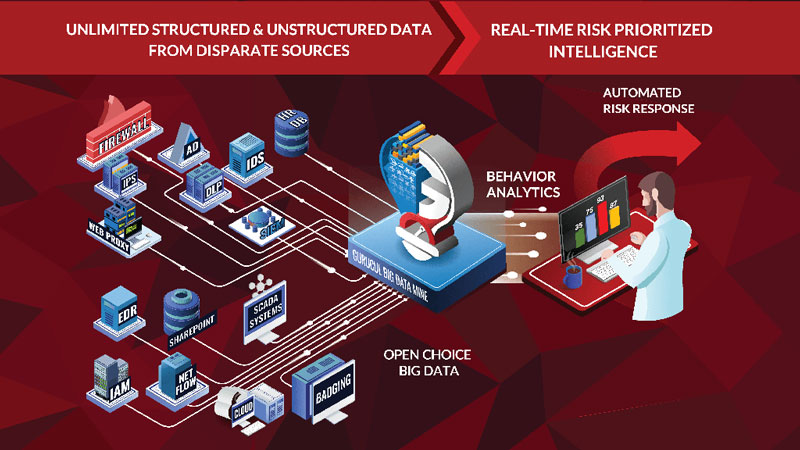
Why Gurucul Behavior Analytics?
Gurucul certainly isn’t the only security analytics company out there. So, why should you choose Gurucul?
Gurucul is big data agnostic – working on your choice big data platform. Also, Gurucul has the largest machine learning library in the galaxy with over 1,300 machine learning models. More behavior models = better coverage.
Gurucul’s Enterprise Risk Engine also provides intelligent prioritized risk scores based on user and entity behavior. Gurucul analytics is powered by robust machine learning models built by data scientists. Whereas our competitors are using signatures, patterns, rules and policies (which can only detect known behavior patterns). Our models go beyond by detecting known or common patterns so you can detect unknown threats.
Gurucul Predictive Security Analytics is SIEM Threat Hunting on Steroids – and it Won’t Break the Bank!
No need to write SQL queries to search the raw or enriched logs with Gurucul. Our contextual search is so effective that it reduces case resolution time by 67%. Our platform is cost effective because we provide open choice of big data and, unlike our competitors, we don’t charge you for it.
Did we mention that our analytics will sit on top of your data lake? You don’t have one, you say? No worries – we will give you one for free!
So, step aside Darwin, the security evolution begins with Gurucul!
Attend the Webinar
Learn more about how Gurucul takes security beyond SIEM with behavior analytics. Join us at our upcoming webinar:
Webinar: Take Security Beyond SIEM with Behavior Analytics
Wednesday, August 19 @ 11:00am PT
The post A Security Evolution: Taking Security Beyond SIEM with Behavior Analytics appeared first on Gurucul.
*** This is a Security Bloggers Network syndicated blog from Blog – Gurucul authored by Jane Grafton. Read the original post at: https://gurucul.com/blog/beyond-siem-behavior-analytics
"behavior" - Google News
August 18, 2020 at 12:30AM
https://ift.tt/34ao2Bk
A Security Evolution: Taking Security Beyond SIEM with Behavior Analytics - Security Boulevard
"behavior" - Google News
https://ift.tt/2We9Kdi
Bagikan Berita Ini















0 Response to "A Security Evolution: Taking Security Beyond SIEM with Behavior Analytics - Security Boulevard"
Post a Comment